Game 3 - CatSeabank
Category
Reverse Engineering
Points
-1
Solves
-1
Tags
We made a game.
https://drive.google.com/file/d/1R5EdsswQydsUQZIToQDkR-1CpwRIzmiK/view?usp=drive_link
In this challenge, we were given a Unity game file and needed to extract the hidden flag through reverse engineering.
Steps to Extract the Flag
- Decompiling the Game
- We can decompile the game using a tool like AssetRipper.
- Extracting the Audio Clip
- From the extracted assets, an
AudioClipdirectory was identified as a potential source of the flag.
- From the extracted assets, an
- Converting to Spectrogram
- The file in
AudioClipwas converted into a spectrogram using a tool likeSonic VisualiserorAudaCity. - The spectrogram revealed the hidden flag embedded within the audio.
- The file in
By analyzing the spectrogram, we successfully retrieved the flag:
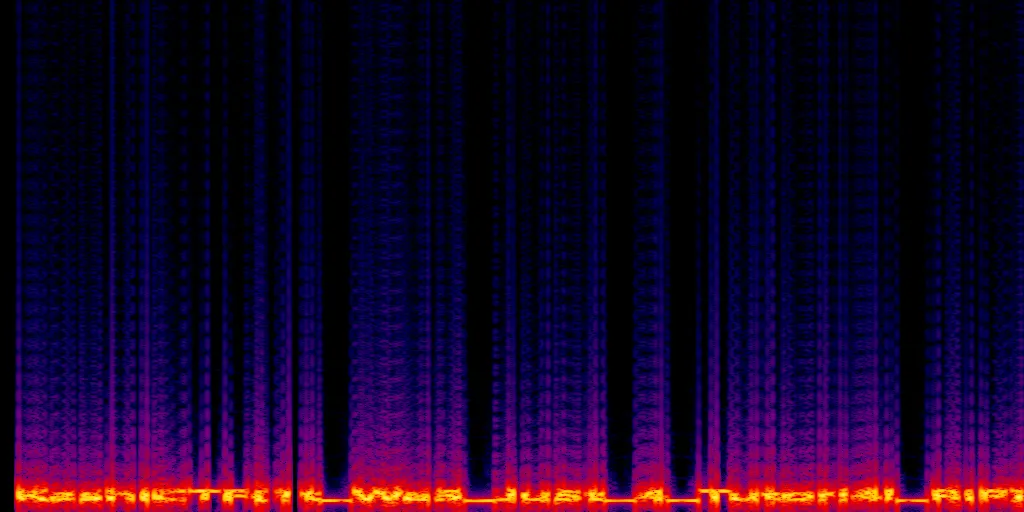
Game 3 - CatSeabank Flag:
KashiCTF{1t_Wa5_Ju5t_4_Tutori4l_RIP}